- Home » News » World News
Manufacturers on Windows XP are risking their systems

Many manufacturers are facing an increased risk of cyber-attacks due to their continuing use of old versions of Windows – especially Windows XP – which are no longer receiving security updates, according to the cyber-security analyst, Trend Micro. In a new report, Trend also warns that the closer links between IT (information technology) and shopfloor networks that are essential to Industry 4.0 are posing increased risks to production processes and intellectual property.
The report, Securing Smart Factories: Threats to Manufacturing Environments in the Era of Industry 4.0, reveals that 4.4% of users in manufacturing industry still rely on Windows XP, which Microsoft stopped supporting in 2014. Although this number may seem small, it is much higher than other industries (2.5%) and leaves users vulnerable to attacks from malware for which Microsoft is no longer providing security updates.
Trend reports that these include old network-based worms such as Downad (also known as Conficker), which it has detected in large numbers in manufacturing environments.
Even manufacturers running more recent versions of Windows may not be applying security patches effectively because they want their systems to operate with minimal interruptions, and regard updates as interfering with business continuity.
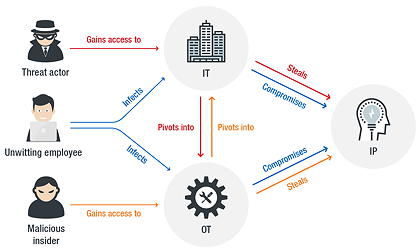
Trend points out that, at the same time, some manufacturers are investing heavily in converging traditional operational technology (OT) with IT networks, which means that previously isolated OT networks are being connected to the IT network to drive efficiencies. This can expose insecure proprietary protocols and potentially decades-old OT equipment that is often not patched frequently enough. It says that there is a “harsh disparity” between the significant operations performed by these systems and the fact that they operate for years with known vulnerabilities.
“Industry 4.0 offers unparalleled opportunities to increase productivity, enhance process efficiencies, and realise on-demand manufacturing, but it also dramatically alters the threat risk model for these facilities,” says Steve Quane, Trend’s executive vice-president for network defence and hybrid cloud security. “As this research outlines, the convergence of IT and OT could unwittingly have a serious impact on production lines, and could lead to the loss of IP and competitive advantage.”
Turning to the types of ICS (industry control system) equipment that could be targeted by cyber-attacks, Trend reports that HMIs are potentially the most vulnerable, with 60.6% of 132 ICS/Scada exploits listed on the ExploitDB database of publicly available exploits. This puts them far ahead of PLCs on 9.8%, IP cameras on 6.8% and gateways on 6.1%.
The cyber-researchers point out that many items of ICS equipment, such PLCs and HMIs, are designed for isolated environments, and therefore may not have adequate cyber-security measures in place. As a result of the increasing connections between OT and IT networks, the ICSs could thus be exposed to the Internet.
According to Trend, the most common security problems affecting HMIs involve memory corruption (stack- and heap-based buffer overflows and out-of-bounds read/write vulnerabilities), poor credential management (use of hard-coded passwords, storing passwords in recoverable format, and insufficiently protected credentials), and a lack of authentication and unsecure defaults (clear text transmission, missing encryption, and unsafe ActiveX controls).
Of 343 ICS and Scada vulnerabilities that have been reported to the US Government’s ICS-Cert (ICS Computer Emergency Response Team) service, Trend found that 12.2% affected Siemens equipment, followed by Rockwell Automation (on 10.5%) and Schneider Electric (9.9%). But it points out that this distribution is “not surprising since these vendors have a wide range of products and the highest market shares in this industry”.
Trend reports that new vulnerabilities are being discovered more frequently than ever before in industrial control systems. For example, zero-day vulnerabilities in HMIs increased by more than 200% in 2018 compared to 2017.
One factor that makes the manufacturing industry potentially attractive for attackers is IP (intellectual property). They could be motivated to steal intelligence on processes, products, or technologies, which may include blueprints of confidential designs, secret formulas or assembly processes. CAD (computer-aided design) or document files, for instance, contain proprietary information, and these can be obtained illicitly and used to produce counterfeit goods, or even infected or trojanised to enable attackers to gain access to critical systems.
Manufacturers, Trend adds, are also being exposed to commodity malware, including cryptocurrency mining attacks that could harm key production processes by consuming processing power and causing network latency. Ransomware is also a major threat to manufacturers if the attack affects production.
To help mitigate the impact of Industry 4.0 threats, Trend Micro recommends that manufacturers restrict user access, disable directory listings, and identify and prioritise key assets to protect.





