- Home » News » World News
ICS cyber-threat numbers fall, but a third are unpatched

The number of “advisories” about cyber-security vulnerabilities in ICSs (industrial control systems) dropped by 9.8% in the first half of 2023 compared to 2022, but more than a third (34%) of the new vulnerabilities do not have any patch or remediation available, compared to just 13% in the first half of 2022.
The figures come from a new report produced by the US industrial asset and network monitoring company, SynSaber, in collaboration with the ICS Advisory Project – an open-source project that provides data from the US Department of Homeland Security’s CISA (Cybersecurity & Infrastructure Security Agency) ICS Advisories visualised a dashboards for use by the OT/ICS community.
The report analyses the Common Vulnerabilities and Exposures (CVEs) reported via CISA ICS Advisories in the first half of 2023, provides insight and identifies trends in the sector, while comparing the first half of 2023 to previous years.
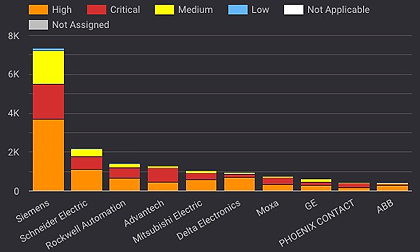
CISA reported a total of 670 CVEs in the first half of this year compared to 681 in 2022. Of these, 88 were rated as being of “critical” severity, 349 as “high”, 215 as “medium”, and 18 as “low”.
Manufacturing and energy were the two critical infrastructure sectors most likely to be impacted by the CVEs reported during the first half of 2023, accounting for 37.3% and 24.3% of the CISA advisories, respectively.
Siemens products received the largest number of CISA advisories (41) of any ICS manufacturer during the first half of 2023.
“The number of CVEs reported is likely to continue increasing over time or at least remain steady,” predicts SynSaber’s co-founder and CEO, Jori VanAntwerp. “It is our hope that this research helps asset owners prioritise when and how to mitigate vulnerabilities.”
ICS Advisory Project: Twitter
CISA: Twitter LinkedIn Facebook





